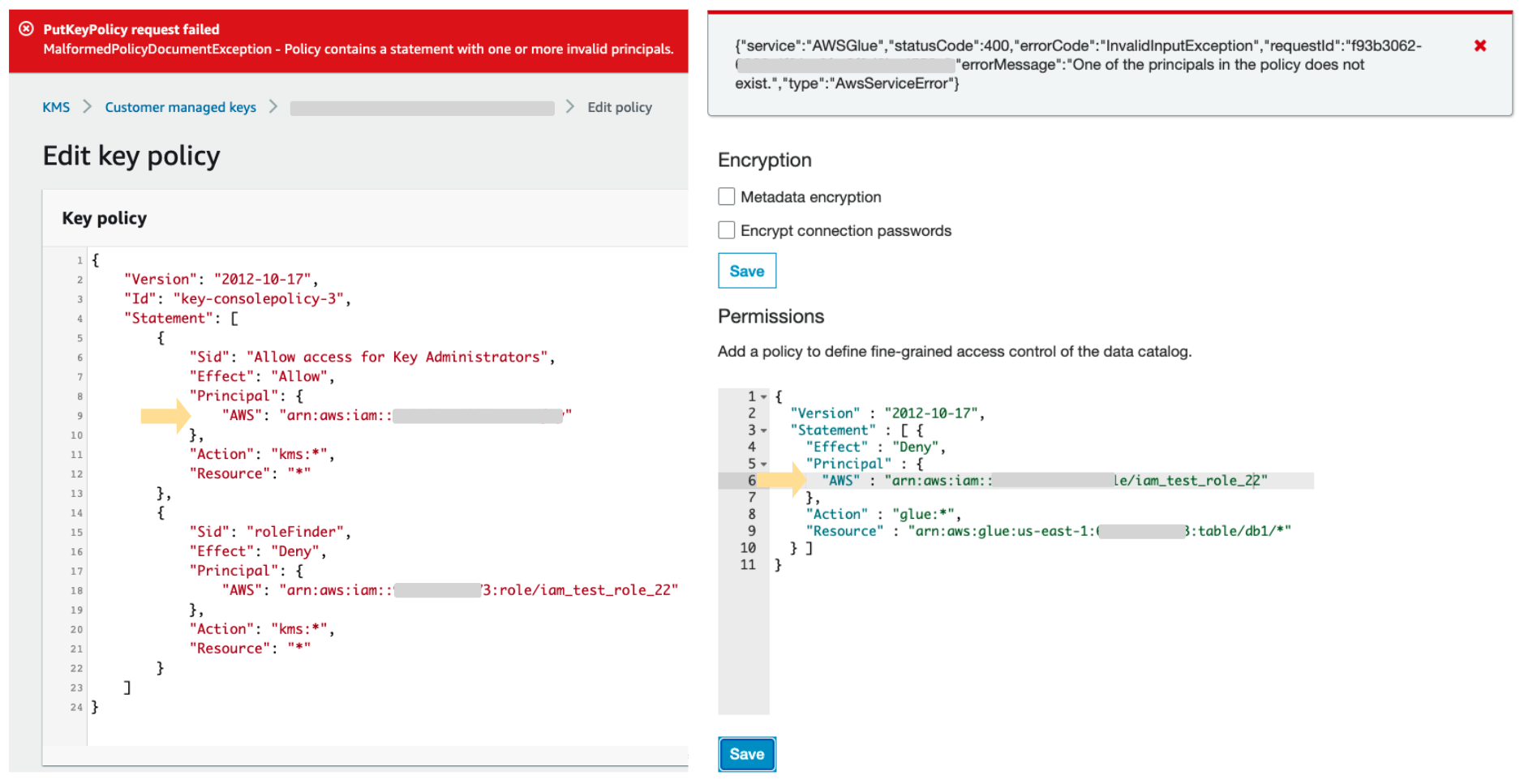
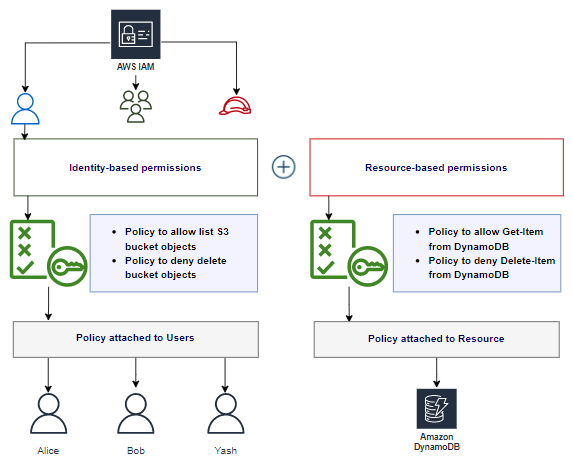
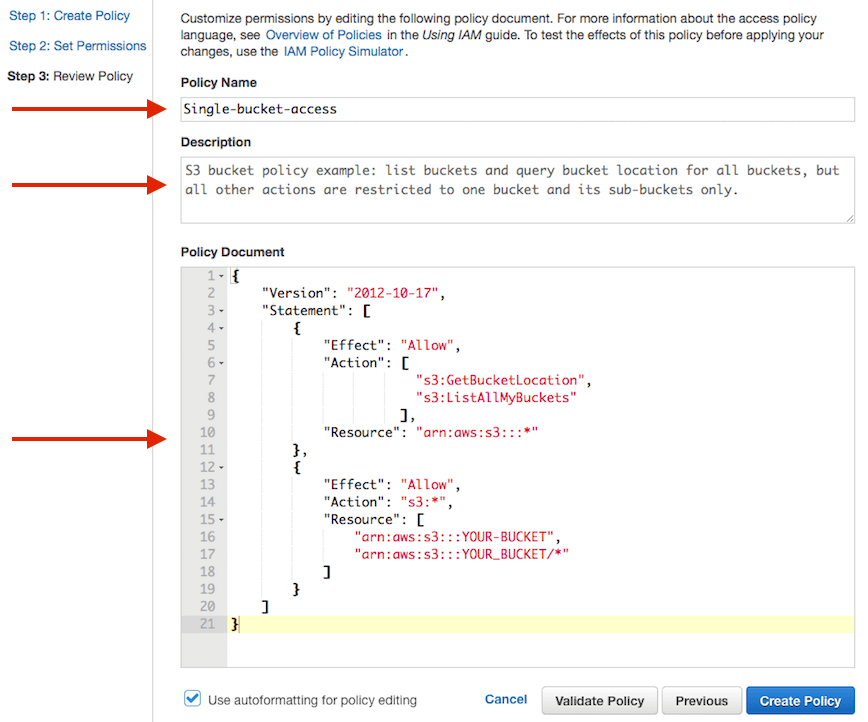
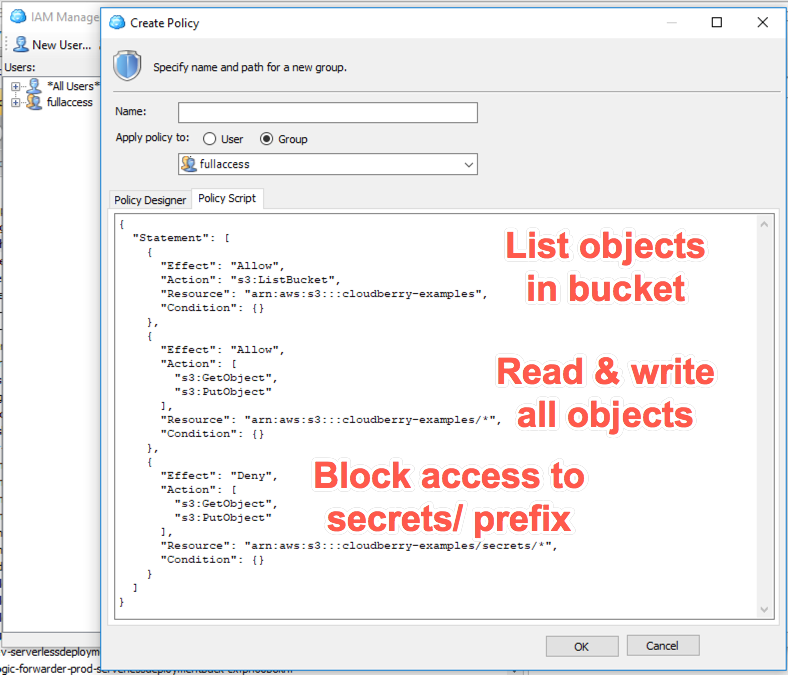
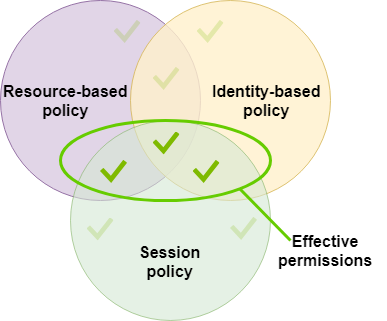
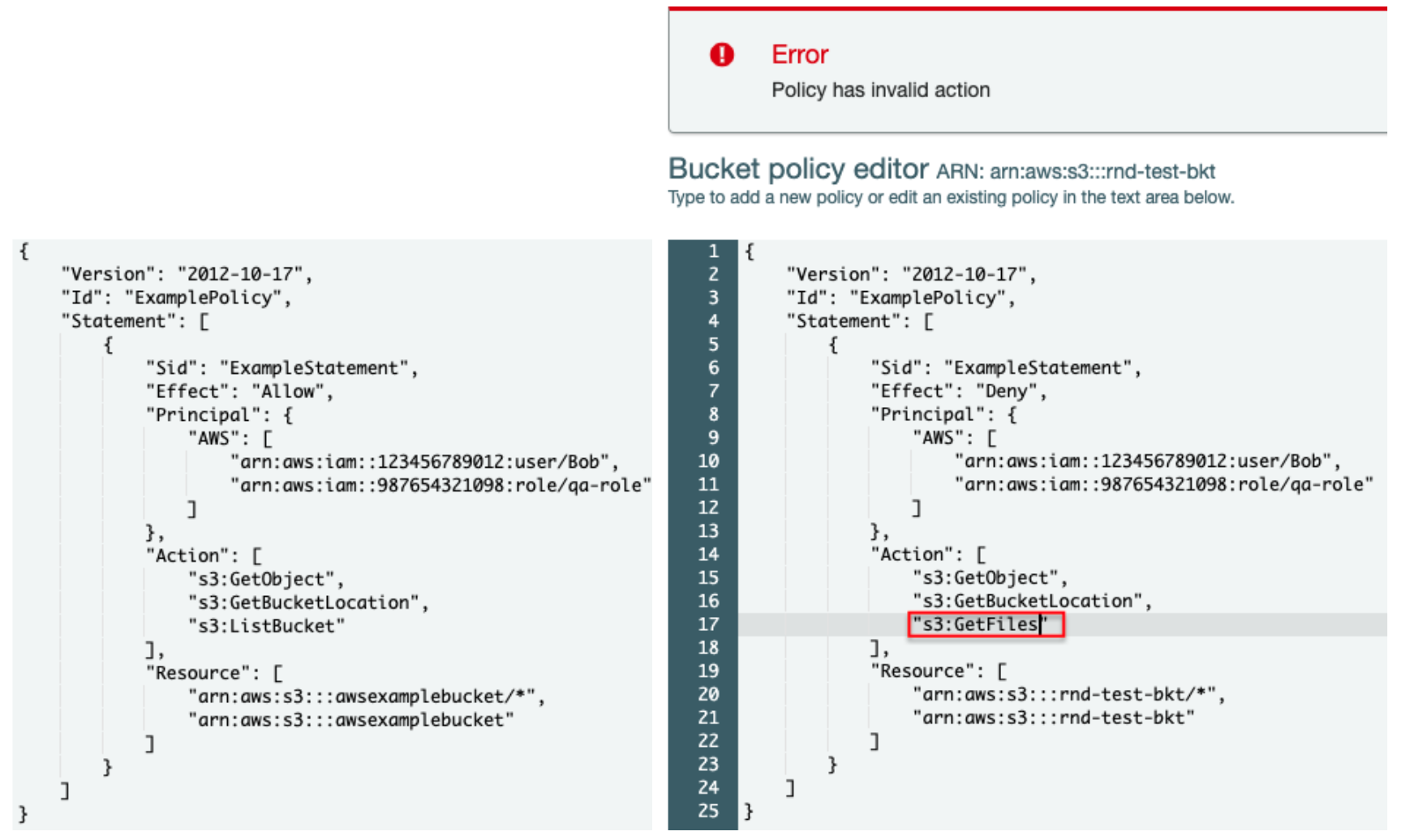
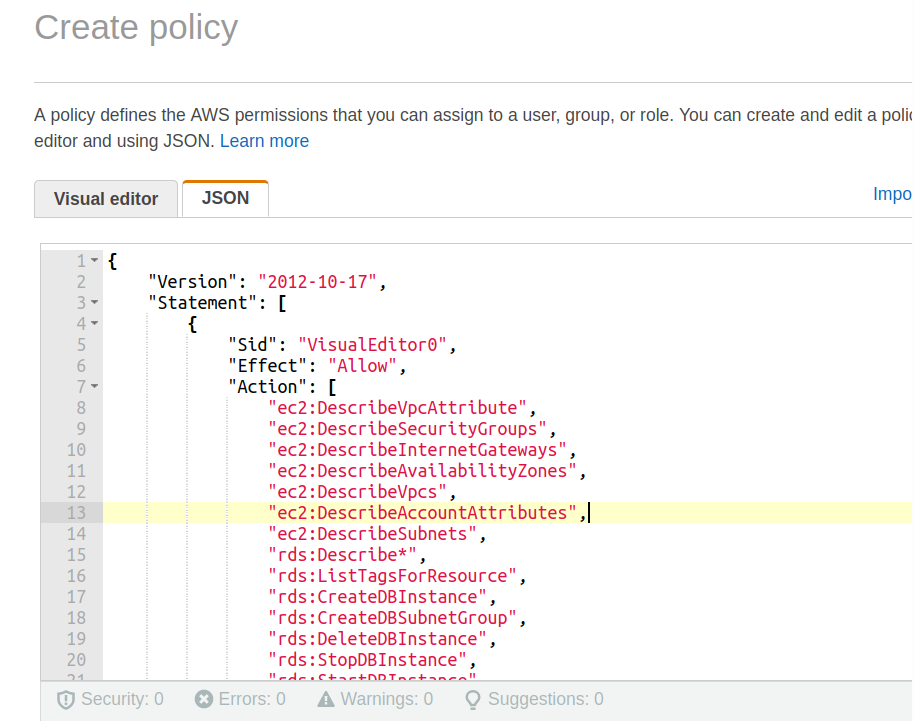
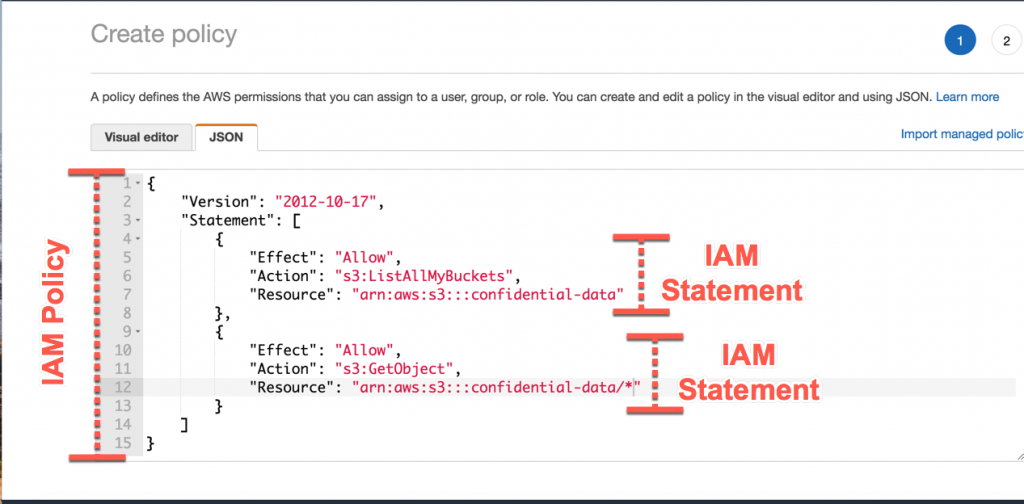
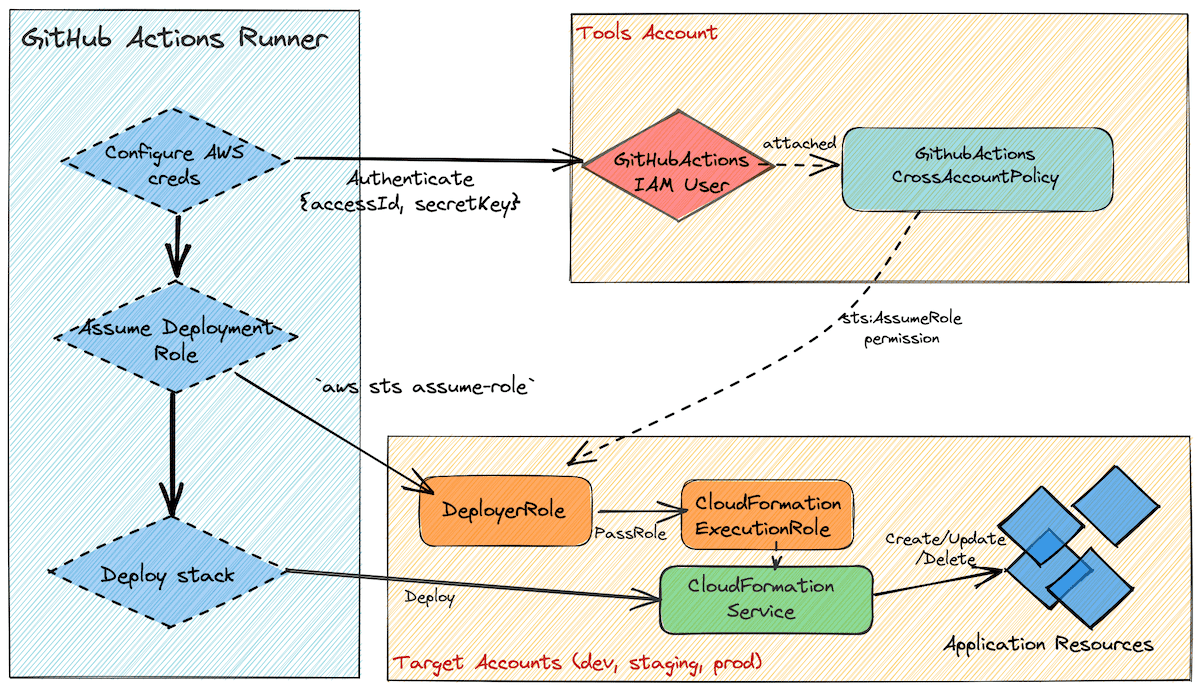
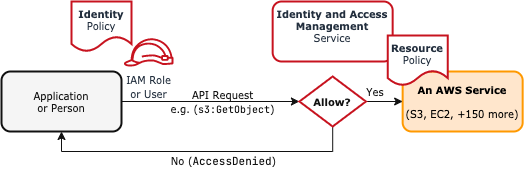
Ben Kehoe on Twitter: "Relevant policy evaluation diagram. Resource policy allows short-circuit the decision before permissions boundaries are evaluated. https://t.co/9EPqorfQv0" / Twitter

How to use resource-based policies in the AWS Secrets Manager console to securely access secrets across AWS accounts | Noise

How to use resource-based policies in the AWS Secrets Manager console to securely access secrets across AWS accounts | AWS Security Blog
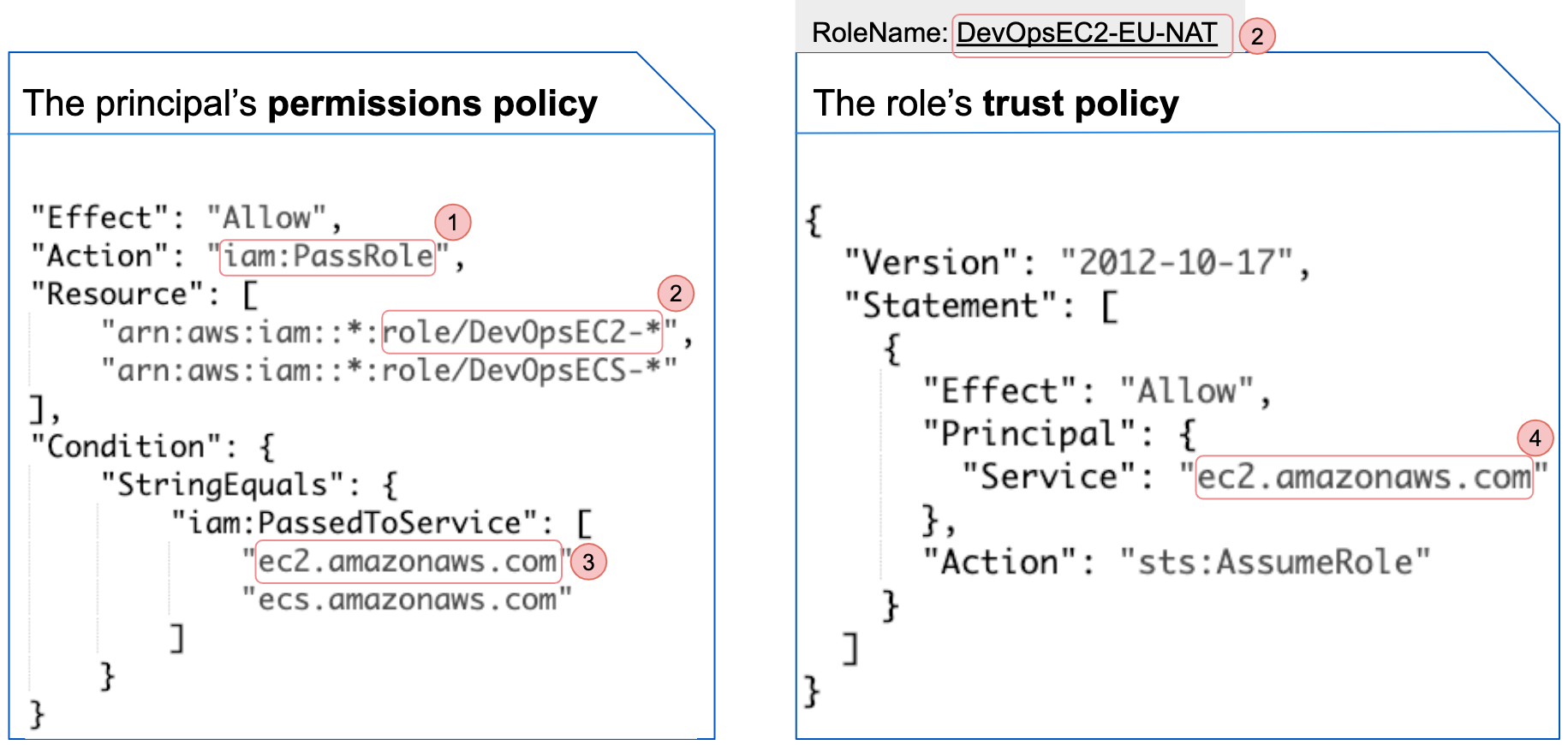
Unit 42 Cloud Threat Report: Misconfigured IAM Roles Lead to Thousands of Compromised Cloud Workloads
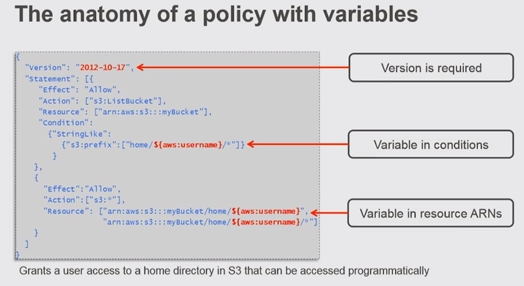
AWS Identity and Access Management (IAM) Policies, sts AssumeRole, and delegate access across AWS accounts - 2021