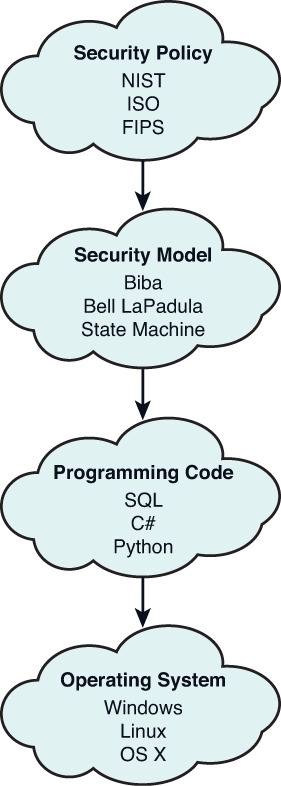
Lecture 2: Security Policy Models Fred Chong CS290N Architectural Support for Secure and Reliable Computing. - ppt download

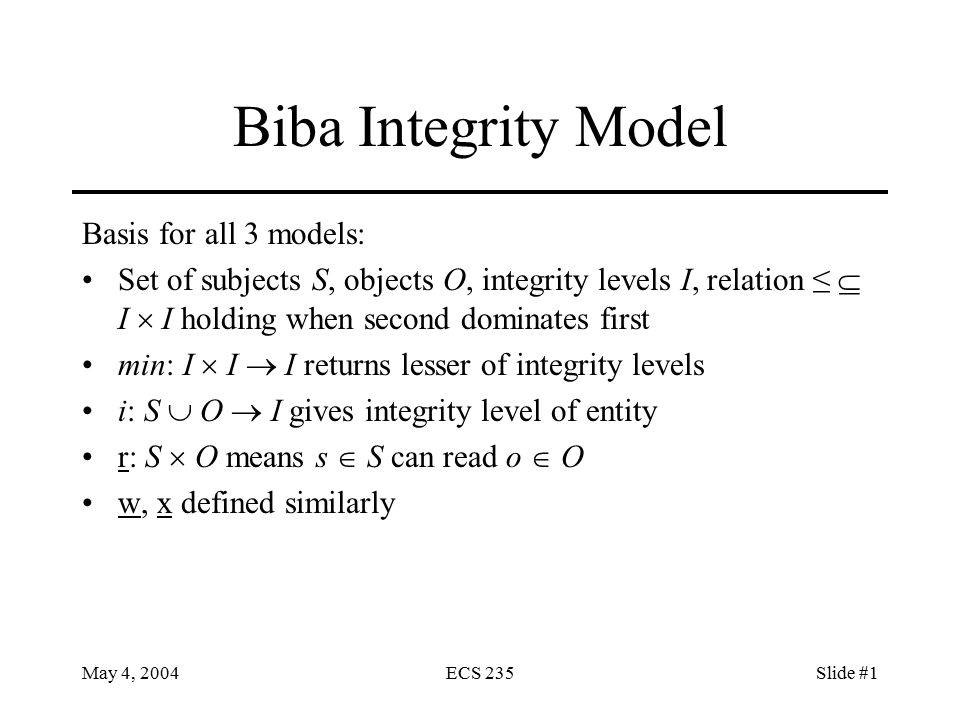
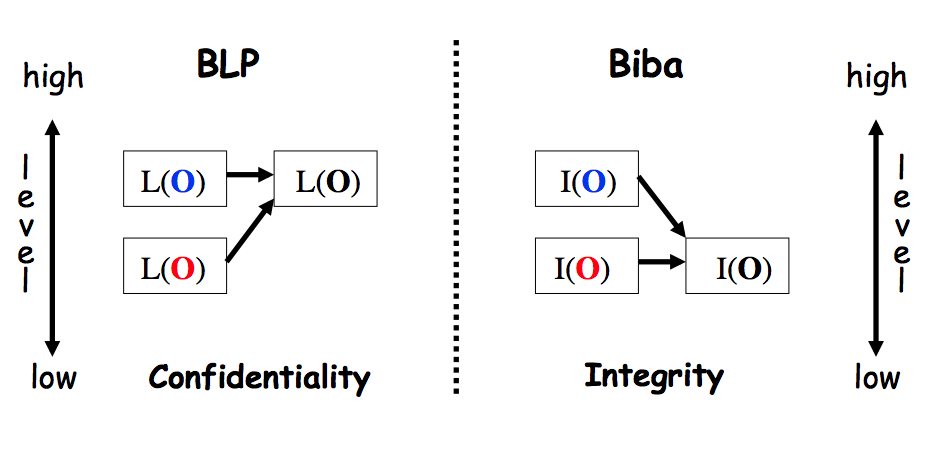
Improved Biba model based on trusted computing - Liu - 2015 - Security and Communication Networks - Wiley Online Library

9 BIBA Kurta Sets From The Amazon Great Indian Festival Sale-2022 to Doll You Up This Navratri | PINKVILLA











![PDF] PRIMA: policy-reduced integrity measurement architecture | Semantic Scholar PDF] PRIMA: policy-reduced integrity measurement architecture | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a5144e59d0a9036885b037ddacbc04effc1405e0/4-Figure2-1.png)